E-shop deployment for IIS
Deployment of eshop on IIS
This document deals with the issue of deploying the e-shop on IIS and the installation of its components and testing.
Before the actual installation of Eshop, it is necessary to have prepared and installed:
- IIS (Internet information service administrator)
- Application server
- Web services server
- PHP version 5.6
Installation and settings of individual components will be described in detail in the following chapters.
IIS Installation
K2 EShop must be used on a server operating system in live operation - Microsoft Windows server. Supported versions of this system are available in “System requirements” document according to K2 IS version. Installation on client operation system is possible but only for test or viewing DEMO installation. This document describes the server installation of IIS and all other system components necessary to run K2 Eshop.
Next step is IIS installation (Internet information service administrator. First is necessary to run Server administrator and then Add role and functionoption.
Picture: Server administrator
First step are instructions before the installation itself, after studying them, move to the next step with the Next button.
Picture: Add guide
In next step user chooses the type of installation - Installation based on role or function.
Picture: Type of installation
Selection of server, where the IIS should be installed.
Picture: Server selection
In next step, in addition to the default checked functions, it is necessary to check the “Web server (IIS)”.
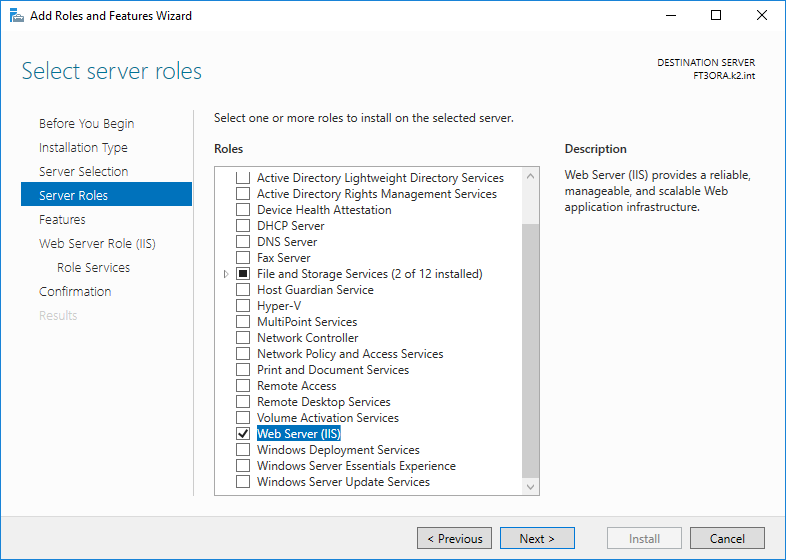
Picture: Server roles
Next step is function definition. User sets Net Framework according to installation and option. Here user needs to keep the default settings and add application development (.NET 4.5, ASP.NET 4.5), Administrative Tools (including IIS 6 compatibility) and Do not check"WebDAV publishing".
Add: ASP.NET 4.6 and under HTTP Activation (under WCF Services).
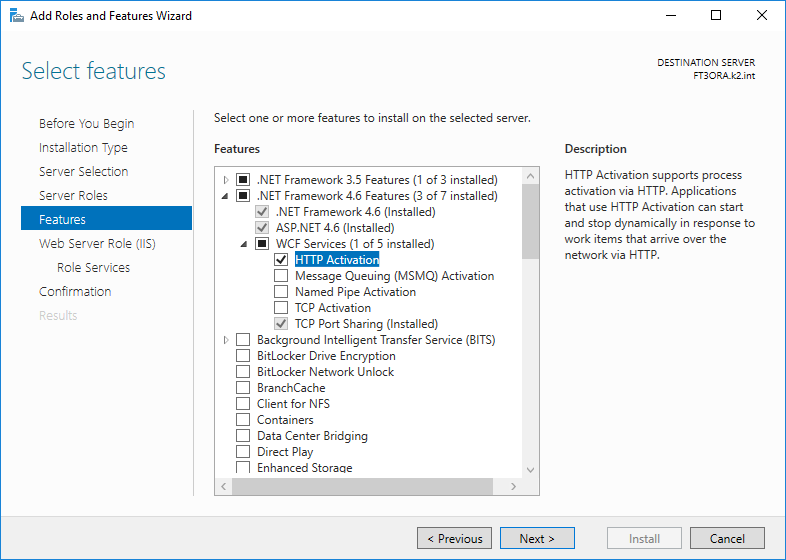
Picture: Function
In next step check CGI (under Application development) - for eshop it is necessary, for SWS not.
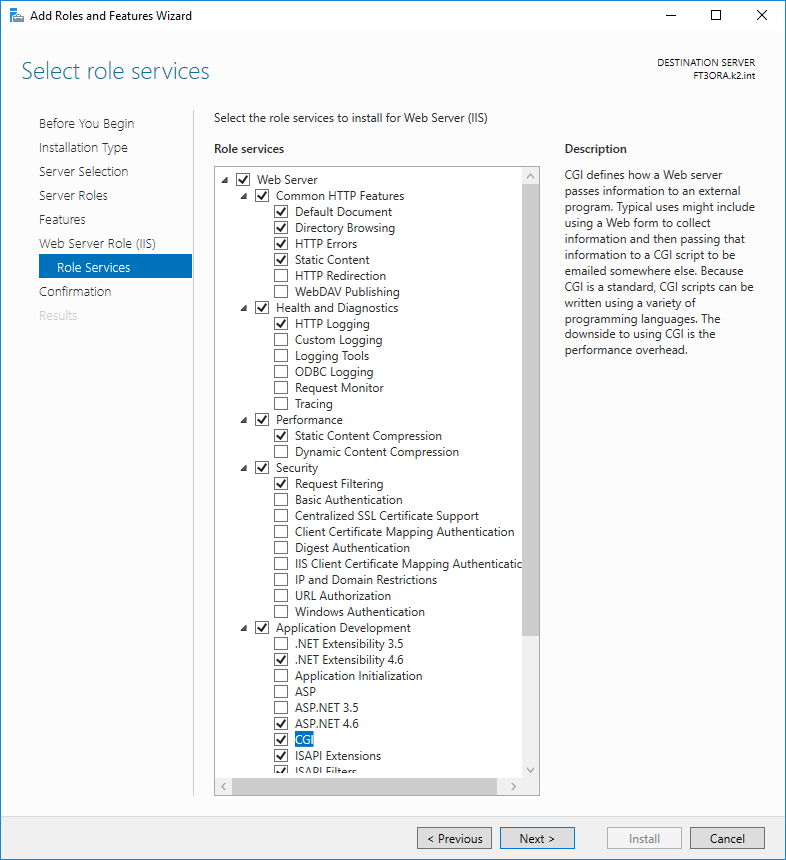
Picture: Role services
In the same step Role services IIS 6 Metabase Compatibility need to be set.
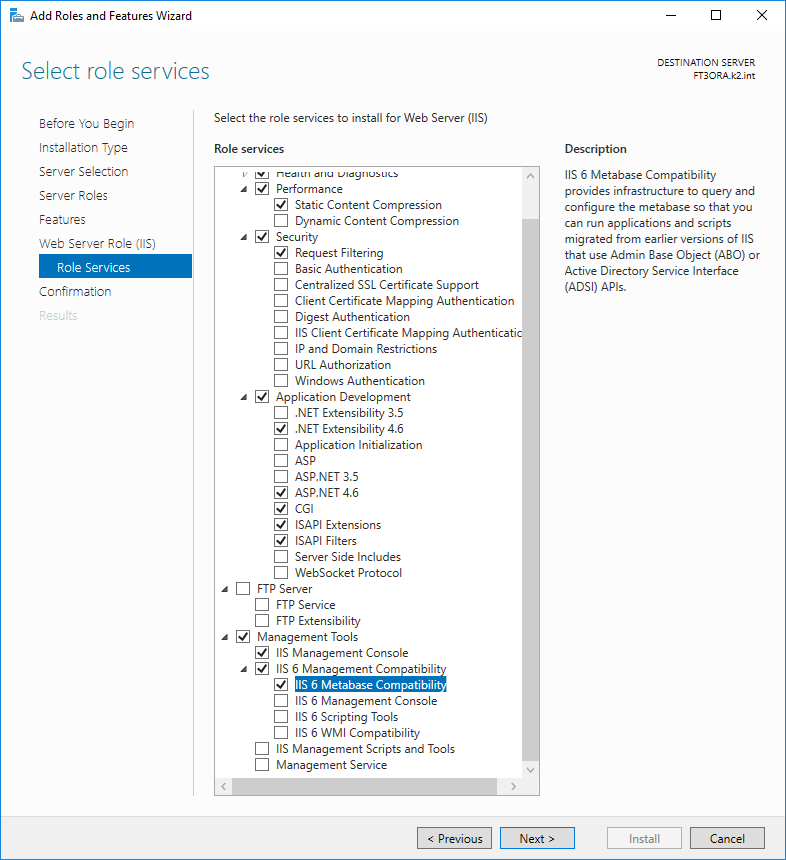
Picture: Role services
In the last step the user confirms previous setting-
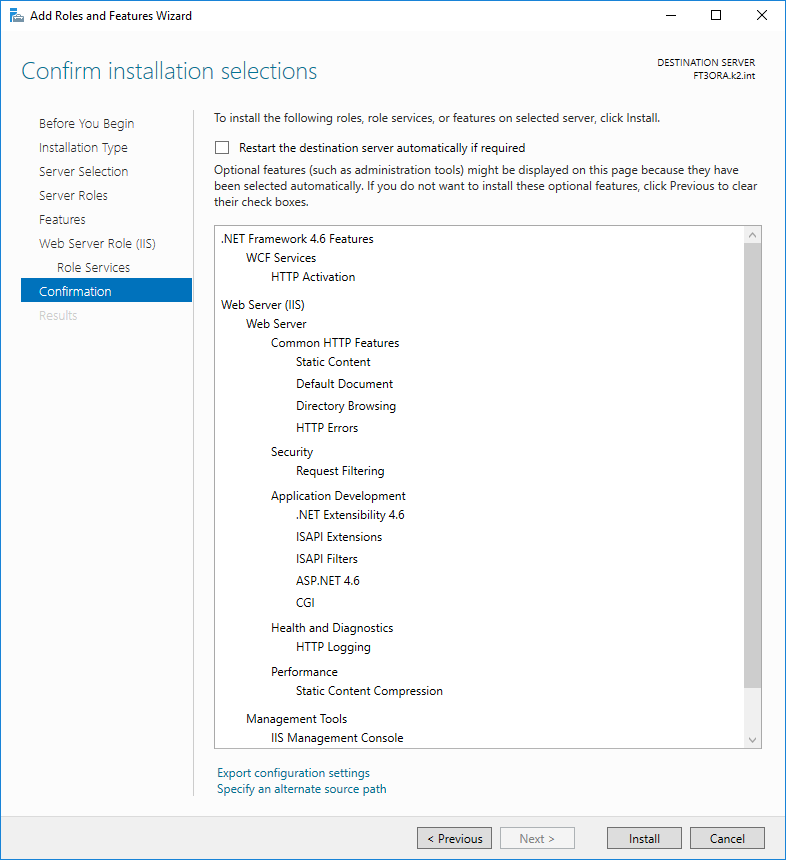
Picture: Installation confirmation
SWS Installation
Server of web services K2 (SWS) is a web application which runs on the web server Microsoft Internet Information Services (IIS). Through the application server K2, it makes the data of the K2 information system accessible and allows running of scripts and reports. Web services are based on the REST technique, i. e. communication is running via HTTP protocol and via standard methods GET (reading data), POST (creating data), PUT (modification of existing data).
Data can be read or sent in XML or JSON format.
After entering the URL root address SWS into the browser, it is possible to browse the basic description of the services and resources/operations using dynamic help.
Installation and basic settings
Prerequisites:
- At least one SWS thread (Number of Shared Users) must be available in theK2 license and the corresponding number of anonymous users with a login composed of the same prefix and a supplemented serial number at the end (e.g. "AN1" - "AN5") must be created in the K2. These users must have the same rights and the same password.
- The installed and running application server with the checked "Configure application server for web services server" and “Configure application server for Eshop during the installation. If this options were not checked during installation, it is possible to add the following parameters in theK2.INI configuration file for an existing AS installation (example for 5 threads and users named AN1 - AN5):
- AS3USER='AN'
- AS3PASSWORD='ANPassword'
- AS3USERS=5
- AS3IO=2000034152
- AS3Contactperson=65 (contact number, which serves as a anonymous users access)
- The server on which the SWS will be installed must have the IIS with installed support of ASP.NET and WCF. When installing IIS, the following components must be selected:
- Roles: Default + Application Development (.NET 4.5, ASP.NET 4.5), Administrative Tools (including IIS 6 compatibility); Don't check: Publishing WebDAV
- Functions: Activation Service (Process Model), WCF Services (HTTP Activation), .NET 4.5, ASP.NET 4.5
- In case of HTTPS installation correctly set certificate in IIS
- In case of publication SWS for internet access, allowed used HTTP / HTTPS ports (80/443 by default)
Recommended deployment for accessing SWS from the Internet:
The K2 application server should always be installed on a server accessible only on the internal network. It is recommended to install K2 SWS and other web applications on a separate server that is accessible from the Internet and has limited access to the internal network allowing only communication with K2 AS.
SWS Installation:
This is done using the K2 Installer. The K2 SWS installation program checks the availability of the basic required components before starting the installation, eventually warns of missing components and the installation is stopped.
You need to enter some information during the installation:
- Target directory - any directory can be selected, it does not have to be in the IIS root directory
- IIS Server Name - enter the name that will be used to access the SWS server. For test installations it is also possible to enter "localhost" - under this name SWS will be available only on the given server.
- Web Site (IIS) - user chooses, to which Web Site he/she wants to install SWS. By default, only "Default Web Site" is available on IIS.
- Application name on IIS - part of the URL address to SWS after the server name. If the name of the server is "mujserver.cz" and user specifies "restservice" as the name of the application, then the basic URL for accessing SWS will be http://myserver.com/restservice
- The name or IP address of the computer where the K2 AS is running
- K2 AS instance name - specified when installing K2 AS
The most common problems with SWS installation and configuration
- Wrong name or IP address of the AS server or wrong name of the AS instance - check and possibly edit it manually in the K2 SWS configuration file - web.config file in the SWS installation directory. Check that nothing is blocking network communication between the SWS server and the AS server
- AS is not configured for SWS - add configuration, see the Prerequisites section above
- Anonymous users are missing or prohibited - see the Prerequisites section above
- There is no number of shared users in the K2 licence or this number is exceeded - update the K2 licence
- Missing IIS components - check IIS components, see the Prerequisites section above
- Missing permission for IIS process (see pict.)
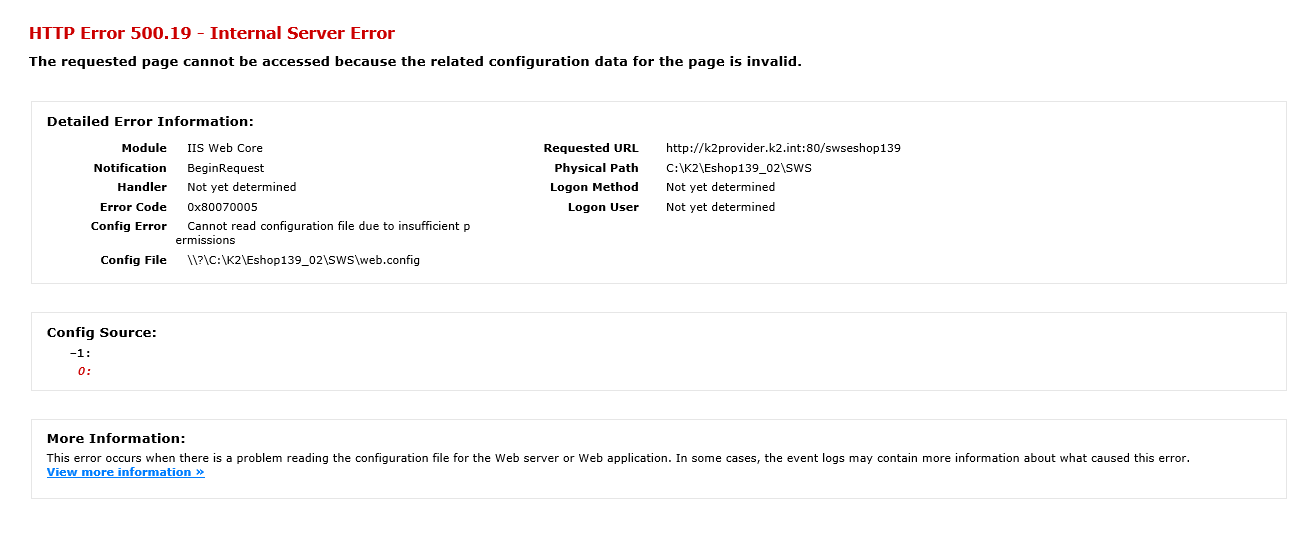
Picture: Missing permission
Permissions must be added to these users.
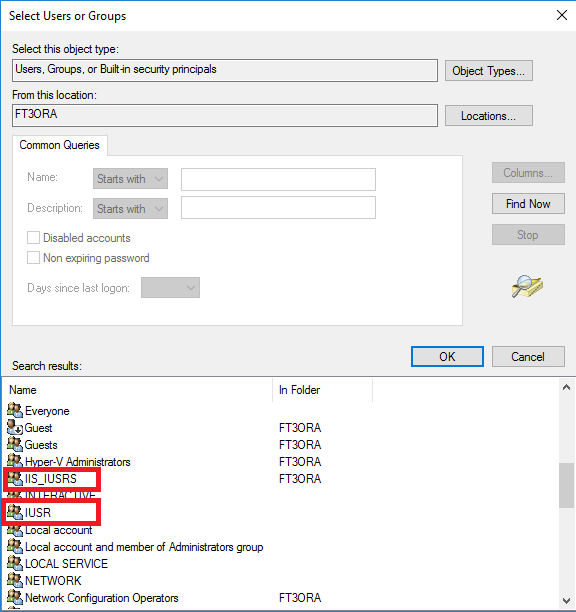
Picture: Users
In most cases logging SWS or AS will help. SWS logging is activated in theweb.config configuration file, using parameters LogPath (log file path), LogLevel (types of messages to be recorded, at least Info is recommended for debugging), LogRequests (allows user to track the processing of individual SWS requests even multiple requests at once).
PHP Installation
Using “WEB platform Instaler” user installs PHP. For eshop it is necessary PHP version 5.6 and higher. For some OS, may not be able to install PHP Manager. It is not a necessary supplement, but it is suitable and recommended.
If the PHP manager cannot be installed, the link below describes how to install it.
Link how to install PHP manager:
https://answers.microsoft.com/en-us/windows/forum/windows_10-other_settings/php-manager-for-iis-on-windows-10/33ef32f0-6a86-4803-abc1-6de81110f9a8?auth=1
Using Web platform instaler user finds PHP 5.6 and starts an installation
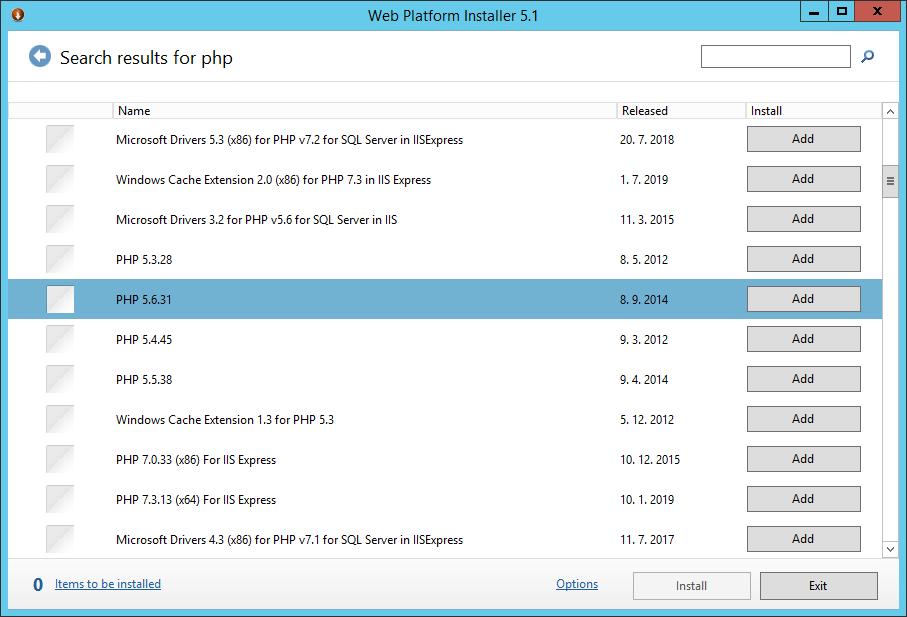
Picture: Installation of PHP version 5.6
Picture: Installation of PHP version 5.6
If PHP manager is installed, it is possible to check if the installation was successful using the Checkphpinfo function.
Picture: Installation verification
If the PHP is installed correctly, following page will display.
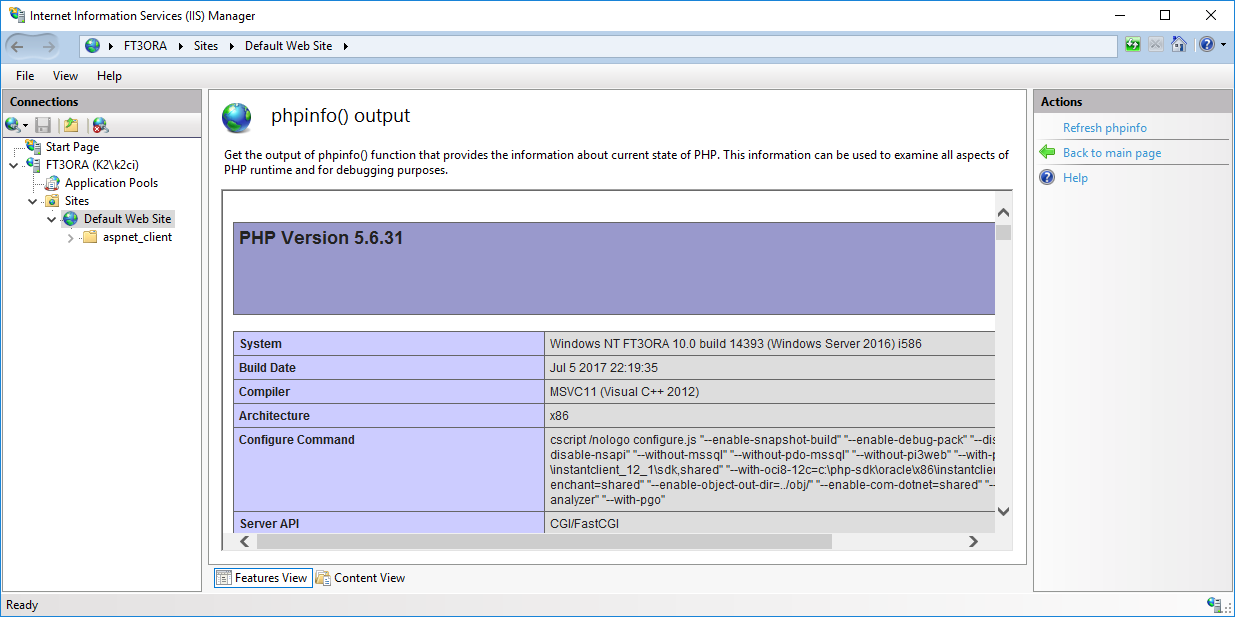
Picture: Installation verification
Secure IIS settings for K2 Eshop
In order to ensure the safest possible operation of K2 Eshop, a web page was created where after entering the URL address of the installed IIS environment or directly to Eshop, verifies whether the environment is set according to recommended configuration.
Web page is available at http://demo.k2.cz/iissecuritychecker/. After opening, a web page will be displayed, see the figure "Test settings for K2 Eshop". In the input field, user enters the address of the server which he/she wants to check for secure settings. For example user wants to check settings of demo installation of K2 eshop - https://demo.k2.cz/eshop/.
The picture shows a computer test on which ISS is running and does not have any of recommendations set.
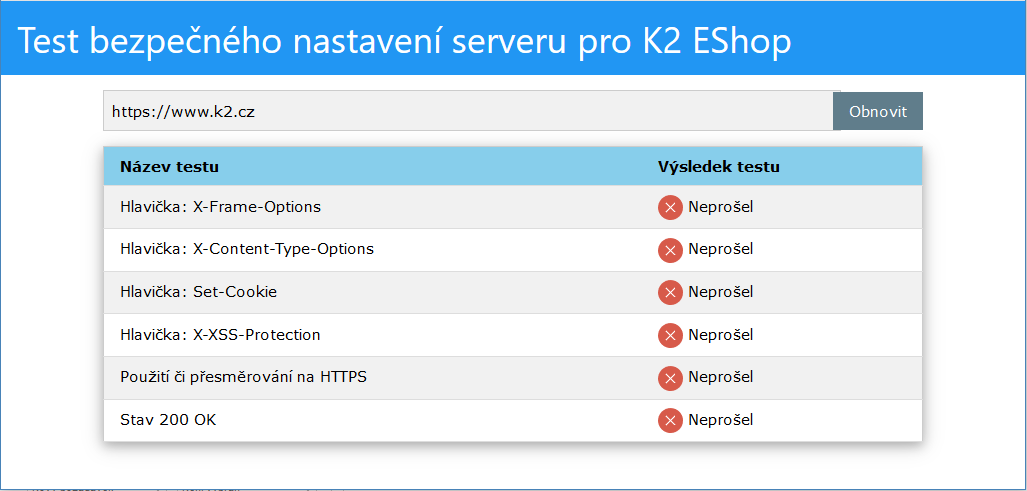
Picture: Test settings for K2 Eshop - incorrect settings
The picture shows the test https://demo.k2.cz , which is set up correctly according to recommendation of safe configuration.
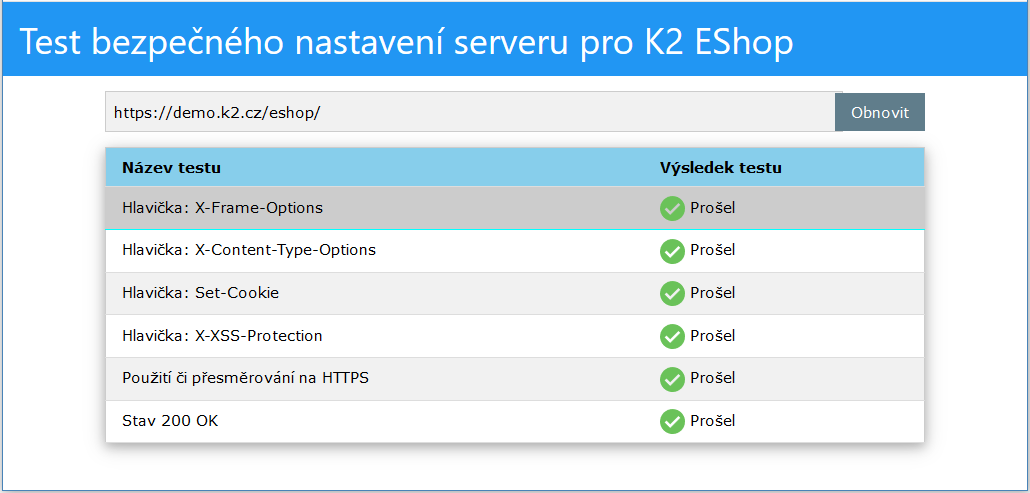
Picture: Test settings for K2 Eshop - correct settings
The test checks the six setting points that are considered appropriate to be set in this way. They increase the secure operation of the e-shop on IIS. The following text of this document deals with individual points, including setting instructions.
IIS settings
For each tested point, its meaning is described here, including a description of why it is appropriate to have it set and what the application is endangered if it is not. The text is also a guide on how to set each of the points correctly.
Note:
IIS server settings are passed from a higher level to a lower one. User can set up the IIS home page, and all others that fbelong under that page will take this setting and use it automatically.
For example, a configuration is defined on the website https://demo.k2.cz, then unless it is specified otherwise, all websites under this, for example https://demo.k2.cz/eshop will have this setting as well. If user runs more e-shops, it is advisable to make the settings at a higher level so that it is used by all installed e-shops on IIS.
Almost all the settings described here relate to the settings of HTTP response headers. User switches to their settings by selecting the website in the tree menu and on the left side of the settings, see the picture. For the selected website, user selects the icon in the right part of the form - "HTTP response headers", see the picture.
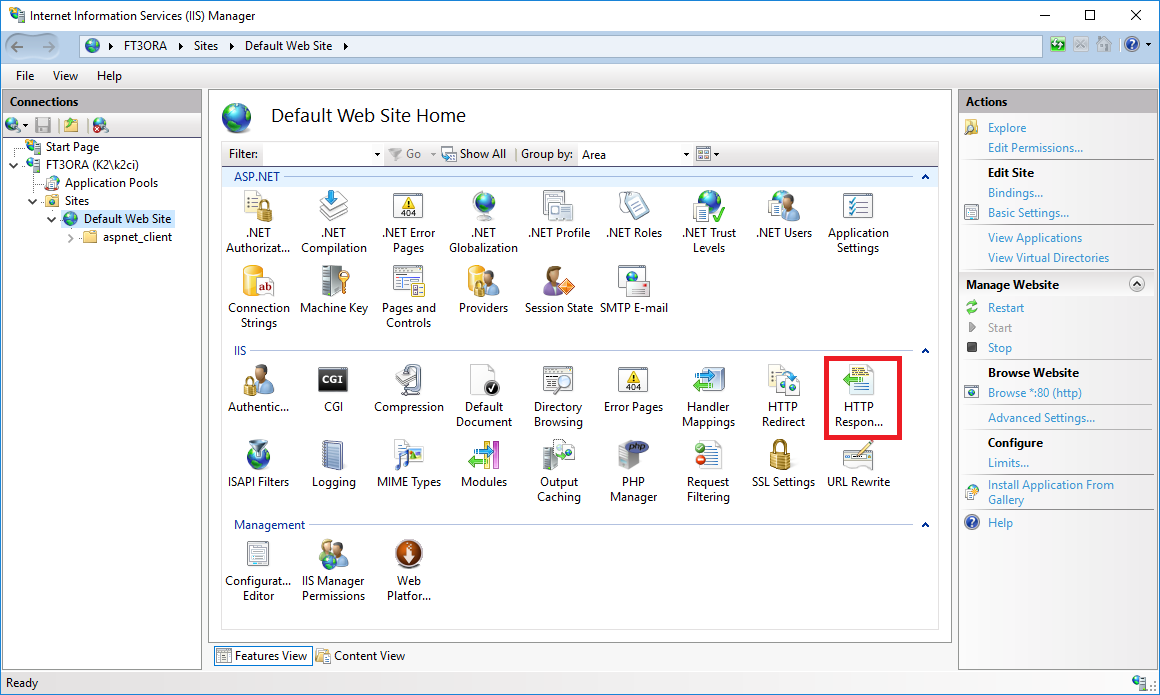
Picture: HTTP response header settings
After opening the settings a form will display (see following picture)
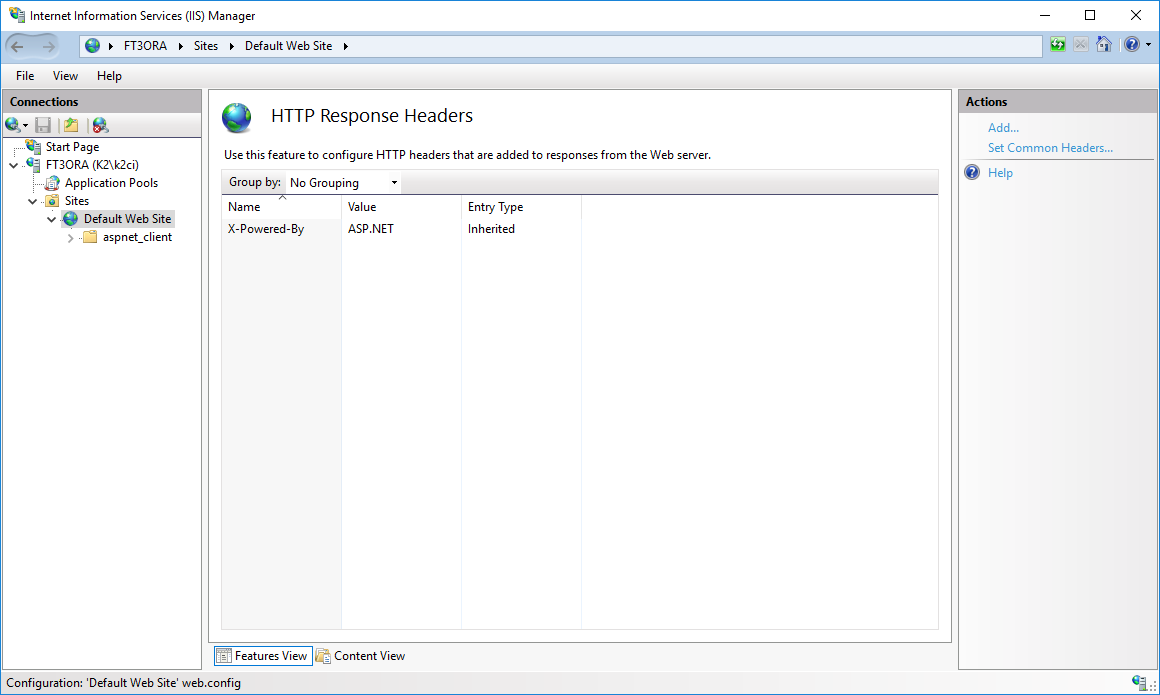
Picture: HTTP response header
In this section user adds individual settings. To do this, right-click and select "Add" from the context menu to open the form for creating a new record, see the picture.
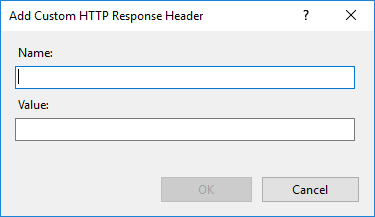
Picture: Adding a new record
Setting up individual parts of IIS
X-Frame-Options Header Not Set
Description of vulnerability
In the HTTP request header is missing the "X-Frame-Options" parameter with the appropriate settings to prevent "ClickJacking" attacks.
A page that uses clickjacking has harmless content in the background - such as funny pictures and a link next to them that claims to lead to another page of pictures. Further, a frame with a completely different page is inserted into the page and it is displayed over the background content, but with transparency turned on, so the user does not know about it. When a user tries to click on a link to lead to another page, he/she are actually clicking on an invisible page at the top. In this way, he/she can perform virtually any action on the target page without his/her knowledge and consent [source: Wiki].
EShop can be inserted into a frame on any page and be exploited.
IIS settings:
- Configuration: HTTP response header
- Name: X-Frame-Options
- Value: DENY
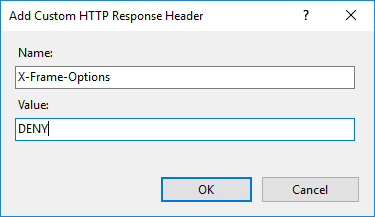
Picture: IIS settings
Changing a settings requires restarting IIS.
X-Content-Type-Options Header Missing
Description of vulnerability
Option „nosniff“ is missing in request „X-Content-Type-Options“ parameter. This vulnerability allows older versions of IE and Chrome to perform "MIME-sniffing", which allows the data to be interpreted and displayed as a content type other than declared.
Repair action
Set the Internet Information Service to add the value "nosniff" to the "X-Content-Type-Options" parameter of the HTTP header. The settings are as follows.
IIS settings:
- Configuration: HTTP response header
- Name: X-Content-Type-Options
- Value: nosniff
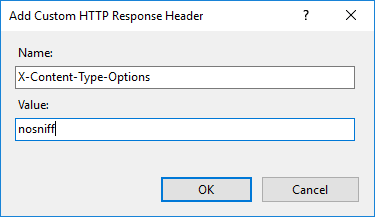
Picture: IIS settings
Changing a settings requires restarting IIS.
Set-Cookie – HTTPOnly a SecureFlag
Description of vulnerability
The cookie is set without the "HttpOnly" label, which means that it can be accessed using JavaScript. Unauthorized access to information may occur.
Repair action
Set the Internet Information Service to add the required "HttpOnly" flag to the HTTP "Set-Cookie" header. Configuration for Internet information service is following.
IIS settings:
- Configuration: HTTP response header
- Name: Set-Cookie
- Value: ^(.*)$ $1;HttpOnly
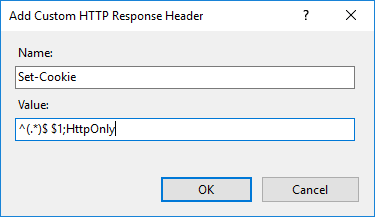
Picture: IIS settings
Changing a settings requires restarting IIS.
Description of SecureFLag vulnerability
Cookies do not have the "Secure" security flag set, which means that they can be accessed over an unencrypted connection.
Repair action
Set the Internet Information Service to add the required "Secure" flag
to the HTTP "Set-Cookie" header.
If the application is accessed using the HTTPS protocol, then everything will work fine. Problems can appear if the certificate expires and the cookie cannot be read from the HTTPS request. If HTTP is used, the cookie value will be empty and EShop will not work in combination with this setting. In general, web applications should run on the HTTPS protocol, which is also a recommendation of K2 atmitec. In the case of debugging and testing on the HTTP protocol, it must be taken into account that "Secure" cannot be set in the Set-Cookie.
IIS settings:
- Configuration: HTTP response header
- Name: Set-Cookie
- Value: ^(.*)$ $1;Secure
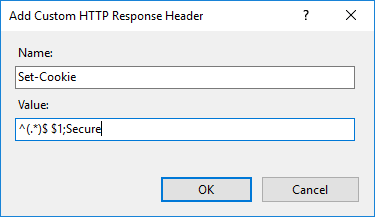
Picture: IIS settings
Changing a settings requires restarting IIS.
These settings can be combined.
The resulting setting value is:
- Configuration: HTTP response header
- Name: Set-Cookie
- Value: ^(.*)$ $1;HttpOnly;Secure
XSS Protection
Description of vulnerability
XSS - "Cross-site scripting" protection of the web browser is not set, or it is disabled by incorrect configuration of the "X-XSS-Protection" function in the HTTP response header on the web server.
Repair action
Set the Internet Information Services to add the "X-XSS-Protection" parameter to the HTTP response header. The Internet Information Services settings are as follows.
IIS settings:
- Configuration: HTTP response header
- Name: X- XSS Protection
- Value: 1; mode=block
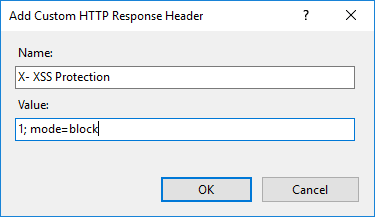
Picture: IIS settings
Changing a settings requires restarting IIS.
Using or redirecting HTTPS
Checking for redirection from HTTPS to HTTP.
Status 200 OK
Checking if the verified page returned HTTP 200 OK, i. e. the page exists and its content is returned.
Summary of secure settings in IIS
The correct setting of all mentioned points should be confirmed by the mentioned test. The form in the picture shows a summary of all points that relate to the setting of the HTTP response header.
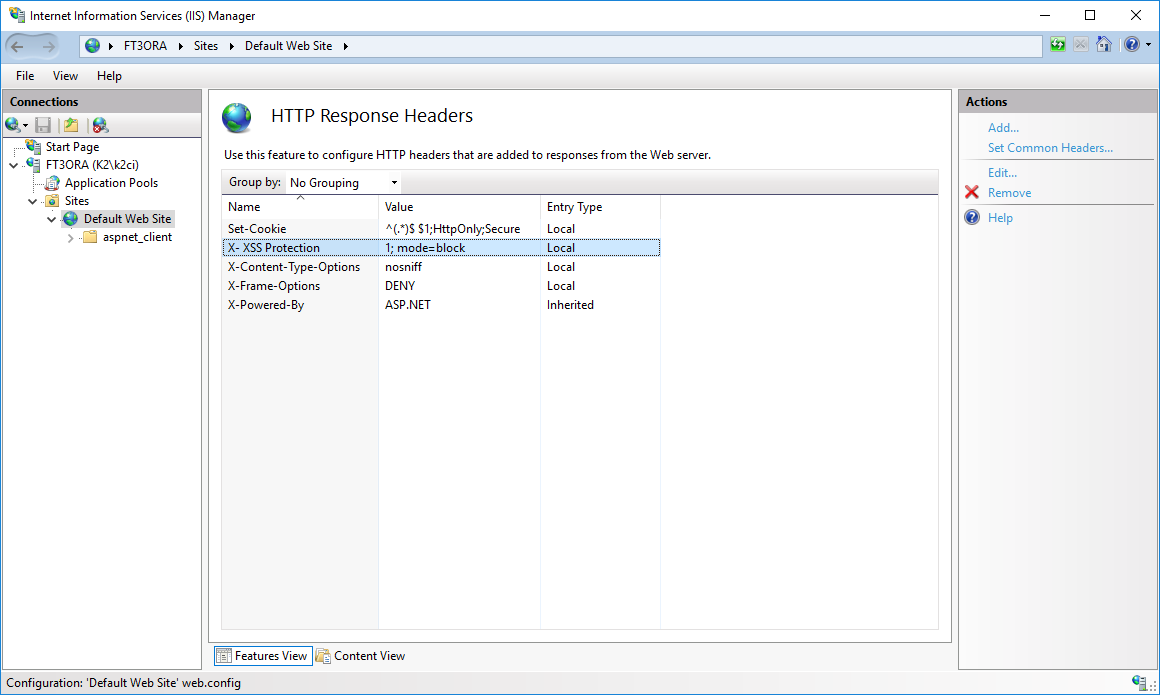
Picture: Parameter settings